Today, the digital world is lifting connectivity and data growth to new heights. While the capabilities and information can give your organization a competitive advantage, this can also open critical infrastructure sectors up to new threats that require cybersecurity mitigations.
As chief information security officers (CISOs) and their personnel continue to elevate in status and importance within their respective organizations, it is becoming increasingly important for security practitioners to write and speak clearly using illustrative language and down-to-earth concepts. They must resist the urge to use heavy technical jargon, and they must develop the ability to listen, translate and speak using the language of business like their executive counterparts.
Throughout the past 10-15 years, regulatory requirements (such as NERC CIP for the power industry) have established basic guidelines for criteria such as cybersecurity, reliability of operations and otherwise. Where things tend to go awry is that the basic guidelines established through regulatory standards are just that: base guidelines, neither prescriptive nor comprehensive.
Base guidelines are a mere subset of what skilled risk managers consider reasonable cyber resiliency. There is most definitely a gap between what is mandated from a regulatory perspective and what is required to meet a minimal viable risk mitigation for the organization.
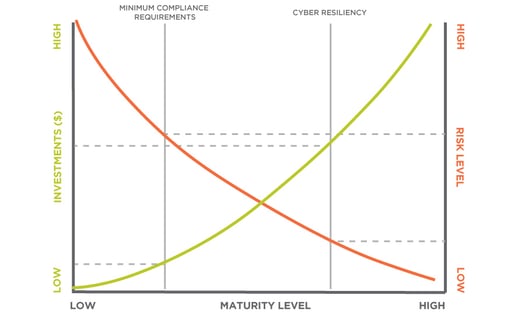 It can be stated that the existence of regulatory guidelines sees that at least some level of risk mitigation is implemented, though. Nonregulated industries are frequently assessed to be in even worse shape. During the same time frame of 10-15 years, we’ve observed that in the absence of a regulatory baseline being established, organizations of nonregulated sectors frequently see cybersecurity purely as a cost or perhaps a surcharge. Consequently, they often choose to forego investment into cybersecurity mitigations. This means that these organizations have little to no cyber risk management in place to fend off cyber-related incidents or to instill a level of resiliency.
It can be stated that the existence of regulatory guidelines sees that at least some level of risk mitigation is implemented, though. Nonregulated industries are frequently assessed to be in even worse shape. During the same time frame of 10-15 years, we’ve observed that in the absence of a regulatory baseline being established, organizations of nonregulated sectors frequently see cybersecurity purely as a cost or perhaps a surcharge. Consequently, they often choose to forego investment into cybersecurity mitigations. This means that these organizations have little to no cyber risk management in place to fend off cyber-related incidents or to instill a level of resiliency.
Meeting Baseline Regulatory Requirements Is No Longer Enough
Given the ever-expanding and intensifying threat landscape, organizations are confronted with an onslaught of threats to their success. Unlike in information technology environments, where the focus remains on data security, cyber incidents within operational technology environments tend to come at a significantly higher impact, cost and consequence — usually involving either impact to operations or worker safety (injury or possibly even death).
Successful intrusions can lead to integrated-system disruptions such as operational systems used for situational awareness and energy trading or can have a more localized impact such as loss of — visibility, control, measurement, safety, mechanical or electrical systems. Organizations with zero security or minimal security are easy targets for would-be attackers.
Given the fiduciary requirements bestowed on CEOs, CFOs and boards of directors for organizations, it is critical that regulated organizations recognize the importance of cyber resilience, and that they avoid settling with a compliance culture. In this context, a compliance culture is characterized by a workforce focused purely on meeting baseline regulatory requirements, nothing more. Organizations must do more than simply conduct compliance checks and file their safety and regulatory documents properly. It is the security professionals’ responsibility to level with executive leadership and convey what is at stake, as well as what must be done to deal with the risk while simultaneously improving organizational resiliency.
Establish a Culture of Resilience
Instead, companies must instill a culture of resilience whereby security improvements are emphasized as a fundamental component of the organizations’ individual corporate cultures. A culture of resilience can establish a set of values and a sense of responsibilities that contribute to protecting company assets and operations from security threats. Perhaps more importantly, these values and responsibilities go above and beyond regulatory requirements, seeing that reasonable cyber resiliency is achieved.
A culture of resilience is attainable through:
- Defining and implementing a minimum viable security standard.
- Investing into training and awareness programs.
- Establishing and tracking incentives for attainment.
- Implementing proper change management programs.
By establishing a culture of resilience, best practices are independent, measurable and usable. Cyber and organizational resiliency becomes a top priority for the organization. Stakeholders can sleep better at night knowing that organizational resiliency is a priority, and that the organization remains vigilant in its focus to eliminate risks to its success.
Regulatory standards and compliance cultures may improve non-incident performance for companies, and that’s not a bad thing. But in today’s environment, the only way to implement cyber resiliency is to improve incident performance, whether the incident represents a cyber-related incident or otherwise. That’s how we mind the gap, and it’s the difference between performing well in good times and performing well no matter what.
A cybersecurity approach founded in the engineering of critical infrastructure allows us to assess your program with an informed eye.




