While no critical network is impervious to cyberattack, comprehensive vulnerability assessments can help organizations keep up with malicious actors by shortening the attack surface and limiting the attack window.
A range of diagnostics, such as GAP or maturity assessments and vulnerability assessments, can help determine a baseline for the current state of the industrial control system (ICS) cybersecurity network. These assessments can also set a baseline for systems or an overarching program.
The GAP/maturity assessments are aimed at identifying and reducing risks by analyzing the current state of the system and then recommending a set of mitigations to be implemented over some time horizon. These mitigations are commonly referred to as a cybersecurity road map.
Vulnerability assessments dive into more granular detail, identifying specific vulnerabilities that exist in network equipment, ICS/SCADA software and systems, operating systems and more. By doing so, we can identify where the weakest links in the system might be, so that a comprehensive plan of action can be developed to mitigate risks.
Multiple Risk Vectors
When it comes to operational technology (OT) environments, it is common for many of the operators and technicians to wear multiple hats for a range of roles, commonly due to a shortage of qualified staffing. The result is a staff that is constantly pressed for time and unable to fully support the needs of the larger business enterprise, sometimes even taking shortcuts without fully considering cybersecurity implications.
At electric utilities, for example, if engineers or technicians at remote substations find themselves in a situation where they lack reliable communications, they may resort to plugging in unauthorized wireless access points to communicate with various devices. While this bring-your-own-device (BYOD) practice may save time and seem like a reasonable solution for the task at hand, the wireless device actually creates a risk vector for the utility’s control network because it is likely unknown and potentially unseen by the utility administrators. Without proper visibility and awareness in place, the device could provide an unexpected access point for an attacker if they happened to be in the right place at the right time.
Solving the issue of visibility and awareness is frequently one of the top issues confronting an ICS cybersecurity program. Because we must know what we have, it’s imperative that we develop an accurate and reliable inventory of current hardware and software assets. As the saying goes, you can’t protect what you don’t know exists.
From there we must understand how vulnerable a particular asset, system or network is. The real issue is to go beyond simply capturing and listing all vulnerabilities or issues. We must use a level of intelligence to provide specific guidance on vulnerabilities or issues that should be addressed in prioritized sequence.
Tightening Attack Windows
Building an accurate OT asset inventory requires a point-in-time asset inventory collection process and it is not uncommon during this step to find internet protocol (IP) addresses that are not listed in previous inventories. This can be due to BYOD practices or other special circumstances. These situations require some investigation to see that the laptop, workstation or other asset is properly identified and not an unsecured rogue device.
This step illustrates another issue of key importance — the need for vulnerability assessments to be performed over a regular and reasonably short time frame.
Attack vectors are constantly evolving, and as devices are added or subtracted from the OT or IT network, actions must be taken to both limit potential attack surfaces as well as the attack window. ICS cybersecurity programs must go further than simply performing activities at a given point in time, filing the data in a file cabinet and resuming day-to-day activities. We live in an era of BYOD and the Internet of Things (IOT), and it is far too easy to gain data and communications pathways into — and out of — these environments.
At a minimum, vulnerability assessments should be performed over a periodic time horizon no longer than 12-18 months. It’s important to remember that the shorter the duration between assessments, the tighter the attack window will be. In addition, the vulnerability assessment should be paired with hardening and/or patching services, based off the findings.
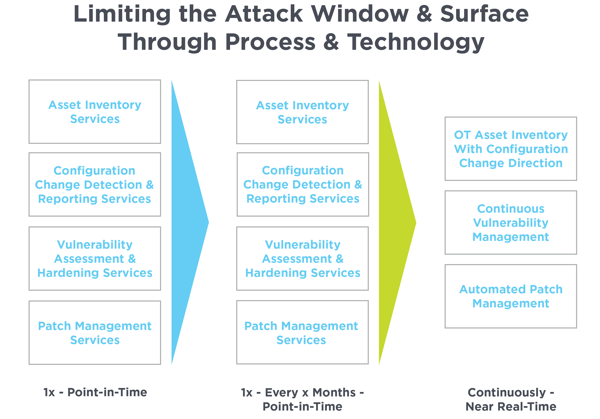
Documenting hardware and software asset inventories provides a good starting point, but companies often manually inventory assets and store information in Excel or similar programs. Best practice is to maintain inventories in a more structured environment, and ideally leverage a form of automation to maintain these inventories daily to limit the attack surface.
With assets identified, manual and automated scans are launched as a second step of the assessment, using proprietary software to identify and detect vulnerabilities. This requires administrative credentials to access the devices inside the network, enabling us to take a detailed look at operating configurations and specific vulnerabilities that may exist or could potentially occur as threats evolve. This process results in a report containing the ranking of most- to least-critical vulnerabilities.
The third step of the vulnerability assessment process is based on the ranking of most critical vulnerabilities. Our list of recommendations often includes some quick wins and easy solutions for remediation of the most critical vulnerabilities through hardening or patch management services. This involves implementing security controls within the network as laid out within the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53 rev 5 or looking at the protection software already in place and working within those parameters first.
The final step in the process is a follow-up meeting to review and discuss the results. It bears repeating that cyberthreats are always evolving, and the snapshot obtained by a single vulnerability assessment needs to be current so that security personnel can strategize and reorient against an ever-evolving threat landscape.
Risk management and resiliency are key for critical infrastructure environments.




