Despite positive steps intended to create better cybersecurity in U.S. Department of Defense (DoD) supply chains, recent events have made it clear that more must be done.
Companies certified in the DoD’s Defense Industrial Base (DIB) must comply with baseline cybersecurity controls to remain in good standing as DoD contractors. The baseline was set in 2016 by the Federal Acquisition Regulation (FAR) 52.204-21. Then in 2018, the Defense Federal Acquisition Regulation Supplement (DFARS), clause 252.204-7012, went into effect. The focus of this supplemental update was on protecting more sensitive information and was seen at the time as a significant advance in DoD supply chain cybersecurity.
However, as cybersecurity breaches have increased in frequency, it has become evident that these measures weren’t sufficient. Adversaries are becoming more advanced and persistent.
It has also emerged that some DIB companies were not complying with all cybersecurity safeguards. Some have been prosecuted under the False Claims Act when prosecutors could present evidence that self-attestations of cybersecurity measures were false.
This combination of factors has resulted in supply chain breaches like the SolarWinds attack, one of several recent events that have imperiled national security and closely held intellectual property.
Maturity Is the Future
With these issues in mind, the DoD looked for a way to mitigate cybersecurity risks within the DIB. The result is the Cybersecurity Maturity Model Certification (CMMC). The CMMC differs from previous policy in both the technical safeguards and the way these are overseen. Instead of a one-size-fits-all checklist, the CMMC aims to align progressively more stringent processes and practices with the types of data available and the types of threats posed.
This progression is represented by maturity levels 1 through 5. This hierarchy establishes a progression of requirements to each level, incrementally adding to those of the preceding levels. For example, reaching maturity level 3 would require a company to meet requirements of levels 1 and 2, plus those imposed under level 3.
Federal Contract Information (FCI) is provided by or generated for the government under contracts to develop or deliver a product or service and does not include information provided by the government to the public (from 48 CFR 52.204-21). This information is not intended for public release.
The CMMC requires DIB companies that process, store or transmit FCI to obtain a maturity level 1 certification. As the base level for CMMC, it is estimated that 60% of all DIB companies will only have to meet level 1 requirements.
Controlled Unclassified Information (CUI) is created or possessed by the government or by an entity on behalf of the government (from 32 CFR 2002.4). Since CUI is considered more sensitive than FCI, the CMMC requirement begins at maturity level 3. Levels 4 or 5 are required mainly for prime contractors who work with CUI and have elevated risks from sophisticated attackers.
No More Trust Without Verification
With implementation of the CMMC, DIB companies will now need to demonstrate compliance with cybersecurity practices and processes to a third-party assessor. Only Certified Assessors (CAs) working for CMMC Third-Party Assessment Organizations (C3PAOs) will be able to perform maturity assessments.
Certificates are granted to the DIB company by the CMMC Accreditation Body (CMMC-AB) only after the CA validates that all practices and processes for the requested maturity level are satisfied. If the CA finds noncompliant controls that can’t be remedied within 90 days, the DIB company will be denied the certification. The certificate must be attained before the DIB company can begin work on a contract in which the CMMC requirement is included.
The DoD and the CMMC-AB recognize the burden this creates for DIB companies and have developed a phased rollout to ease the transition. Beginning in 2021, only 15 new DoD contracts will have the CMMC requirement included. As a result, the DoD estimates that about 900 companies will work with FCI and need to achieve a level 1 certification before beginning work on these 15 contracts. Since a majority of DIB companies only work with FCI, the estimated number of DIB companies that work with CUI will only be about 450. In the coming years, more contracts will include the CMMC requirement and therefore more DIB companies will need the certification (see Figure 1). Beginning in Fiscal Year 2026, every new DoD contract will have a CMMC requirement.
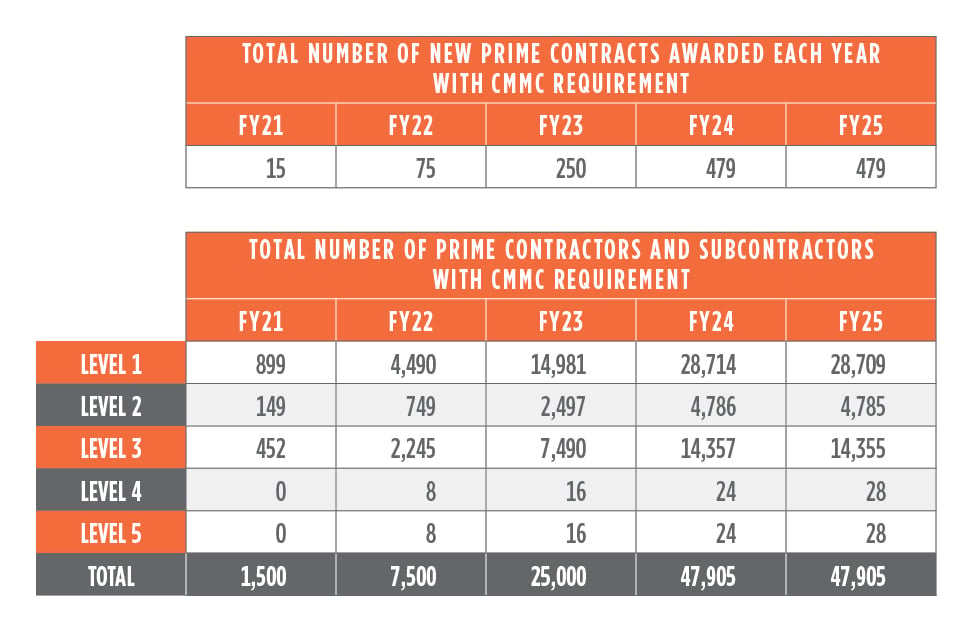 Figure 1: Overview of five-year CMMC rollout. Source: DoD Chief Information Security Officer for Acquisition and Sustainment.
Figure 1: Overview of five-year CMMC rollout. Source: DoD Chief Information Security Officer for Acquisition and Sustainment.
Plan Early to Create CMMC Success
To paraphrase an old aphorism: Failing to plan is planning to fail. This is especially true with CMMC compliance because of the emphasis on maturity and the evidence required to validate that maturity. Writing policies and procedures will take time, and DIB companies must identify the technological tools and personnel to implement them. From a company’s financial standpoint, efficient budgeting for all these activities is significantly easier when more lead time is allowed. Having a CMMC certification already in hand could be a key differentiator on competitive DoD contracts.
While the DoD contracting requirement is the largest factor for DIB companies, the potential return on investment for pursuing certification under CMMC has other considerations as well. The General Services Administration has included CMMC cybersecurity standards in a $50 billion governmentwide acquisition contract. The Department of Homeland Security has also been targeted as the next major agency to implement CMMC into its contracts. These expansions of CMMC requirements mirror the pattern of DoD leading the way in technology in the public and private sectors. In fact, industry experts expect CMMC requirements will continue to spread through all federal agencies and even to state and local agencies.
Help Is Available
If CMMC certification is likely to be needed, 1898 & Co. is a CMMC Registered Provider Organization. Determining the appropriate scope and maturity level takes perspective and experience with the type of information that will be exchanged or possessed on behalf of the DoD. A gap analysis may be needed as a foundation for a tailored road map to the desired CMMC maturity level. You don’t have to go it alone.
Cyber resilience requires a balance of mitigation measures to achieve optimal risk management.




